When first I haerd about azure Governance a lot come to my mind and I had a lot of ideas ,what do they mean ? and what is Governance in the cloud, until I found this simple definition :
Governance refers to the ongoing process of managing, monitoring, and auditing the use of Azure resources
So Governance in azure mean managing resource organisation and security ,auditing and monitoring cost , or we can say too “Putting the Right Controls in Place to Ensure Your Company Reaps the Rewards of Cloud Migration”
To create a plan for Azure cloud governance, it is important to have a detailed understanding of the current people resources, processes and technology frameworks used .
So we need to manage (subscriptions,managment groups,resource groups) apply a couple of security rules for (acces control,resource locks and policies) ,audit activities and azure alerts and monitor azure cost .
In this blog post we are going to see what is Azure Policy ,how to create a couple of policies ,reasons and how to apply them .
so let’s start .
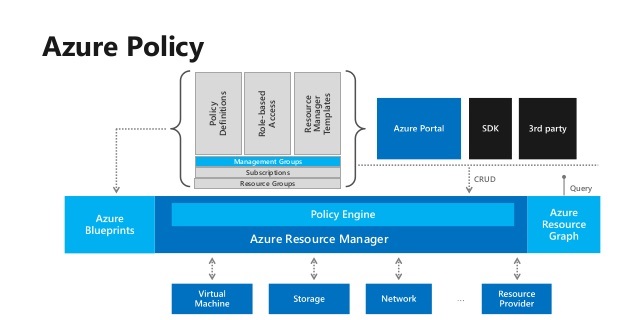
what are azure policies ?
Azure Policy is a service in Azure that you use to create, assign, and manage policies. These policies enforce different rules and effects over your resources, so those resources stay compliant with your corporate standards and service level agreements. Azure Policy meets this need by evaluating your resources for non-compliance with assigned policies. All data stored by Azure Policy is encrypted at rest.
For example, you can have a policy to allow only a certain SKU size of virtual machines in your environment. Once this policy is implemented, new and existing resources are evaluated for compliance. With the right type of policy, existing resources can be brought into compliance.
Policy definition :
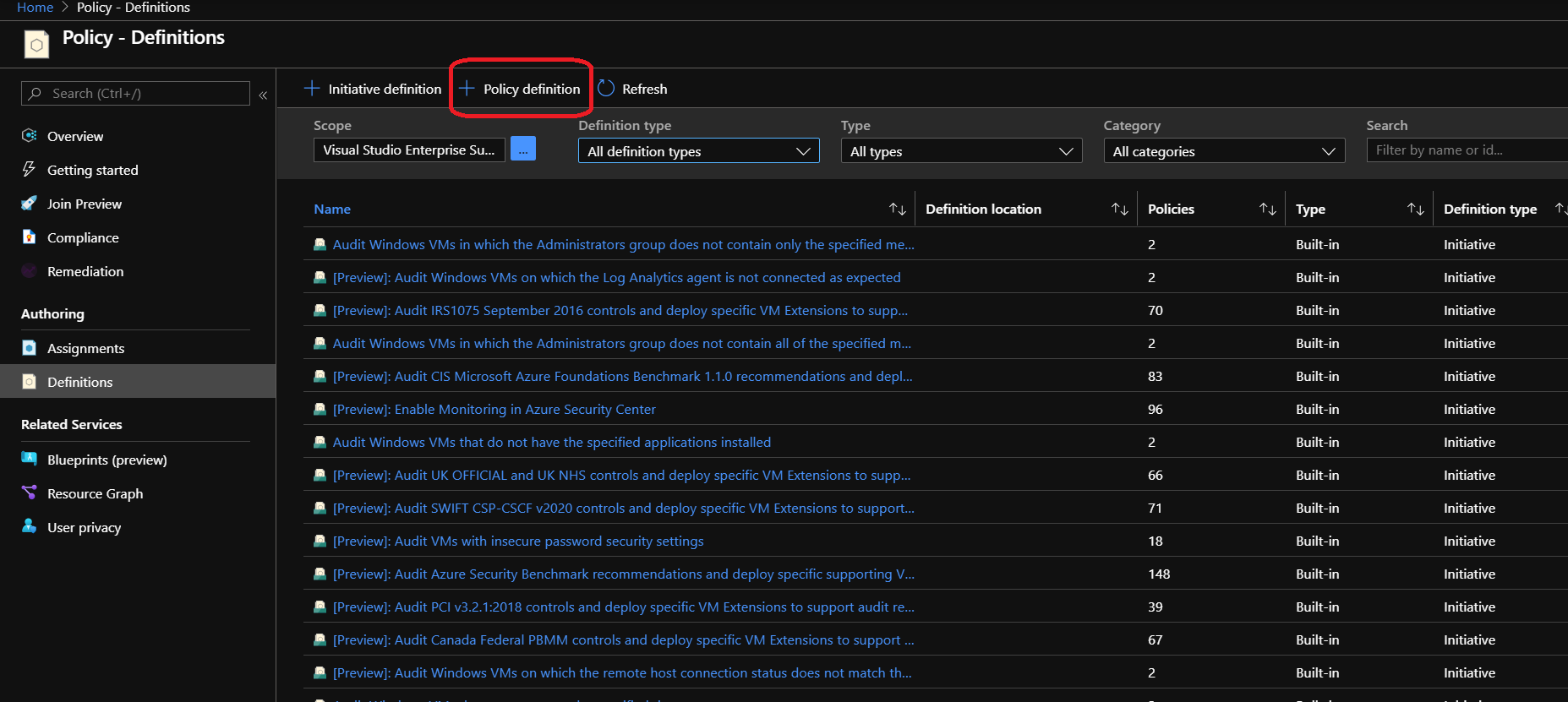
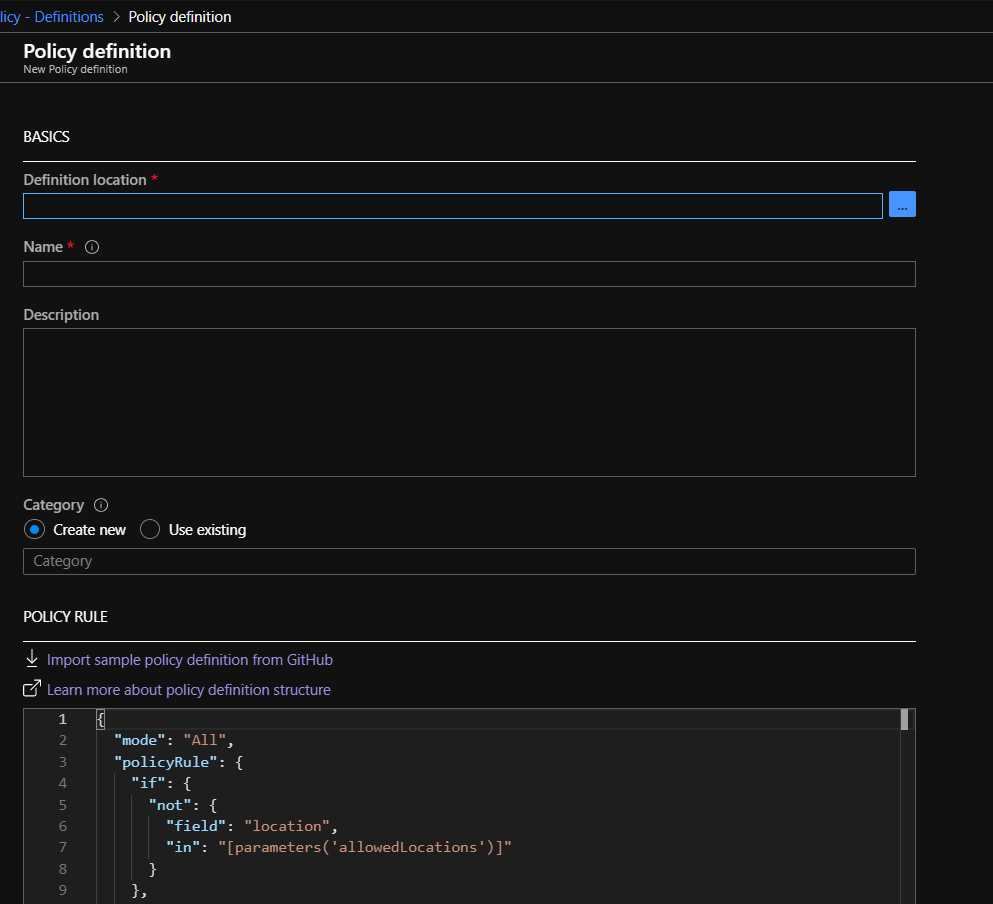
To implement/apply a policy in Azure Policy we need to start by creating a policy definition .
Policy definitions describe resource compliance conditions and the effect to take if a condition is met.
So ,a policy provides control and governance over the resources themselves (i.e. restricting which geographies and regions a virtual machine can be deployed to, or what SKU of virtual machines can be deployed). You can create these policies, and then apply them to a Management Group, Subscription, or a Resource Group.
Conditions :
A condition evaluates whether a field or the value accessor meets certain criteria and we are going to take effect or decision depend on that condition . The supported conditions are :
>"equals": "stringValue" . >"notEquals": "stringValue" >"like": "stringValue" >"notLike": "stringValue" >"match": "stringValue" >"matchInsensitively": "stringValue" >"notMatch": "stringValue" >"notMatchInsensitively": "stringValue" >"contains": "stringValue" >"notContains": "stringValue" >"in": ["stringValue1","stringValue2"] >"notIn": ["stringValue1","stringValue2"] >"containsKey": "keyName" >"notContainsKey": "keyName" >"less": "value" >"lessOrEquals": "value" >"greater": "value" >"greaterOrEquals": "value" >"exists": "bool"
You can read more here https://docs.microsoft.com/en-us/azure/governance/policy/concepts/definition-structure
Effect :
Depends on the condition that we are going to write , we are going to take effect , the available effects are :
Append: adds the defined set of fields to the request Audit: generates a warning event in activity log but doesn't fail the request AuditIfNotExists: generates a warning event in activity log if a related resource doesn't exist Deny: generates an event in the activity log and fails the request DeployIfNotExists: deploys a related resource if it doesn't already exist Disabled: doesn't evaluate resources for compliance to the policy rule EnforceOPAConstraint (preview): configures the Open Policy Agent admissions controller with Gatekeeper v3 for self-managed Kubernetes clusters on Azure (preview) EnforceRegoPolicy (preview): configures the Open Policy Agent admissions controller with Gatekeeper v2 in Azure Kubernetes Service Modify: adds, updates, or removes the defined tags from a resource .
More details you can read here . https://docs.microsoft.com/en-us/azure/governance/policy/concepts/effects
So let’s start by writing some policies .
Policy 1 Allowed locations for resource group:
Let’s say you have a rule on your company that the created resource groups must be only created in france ,how to define this policy ? :
{
"mode": "All",
"policyRule": {
"if": {
"allOf": [
{
"field": "type",
"in": [
"Microsoft.Resources/subscriptions/resourceGroups"
]
},
{
"not": {
"field": "location",
"in": "[parameters('allowedLocations')]"
}
}
]
},
"then": {
"effect": "deny"
}
},
"parameters": {
"allowedLocations": {
"type": "Array",
"metadata": {
"displayName": "Allowed locations",
"description": "Allowed locations for resource groups-demo",
"strongType": "location"
}
}
}
}
Steps :
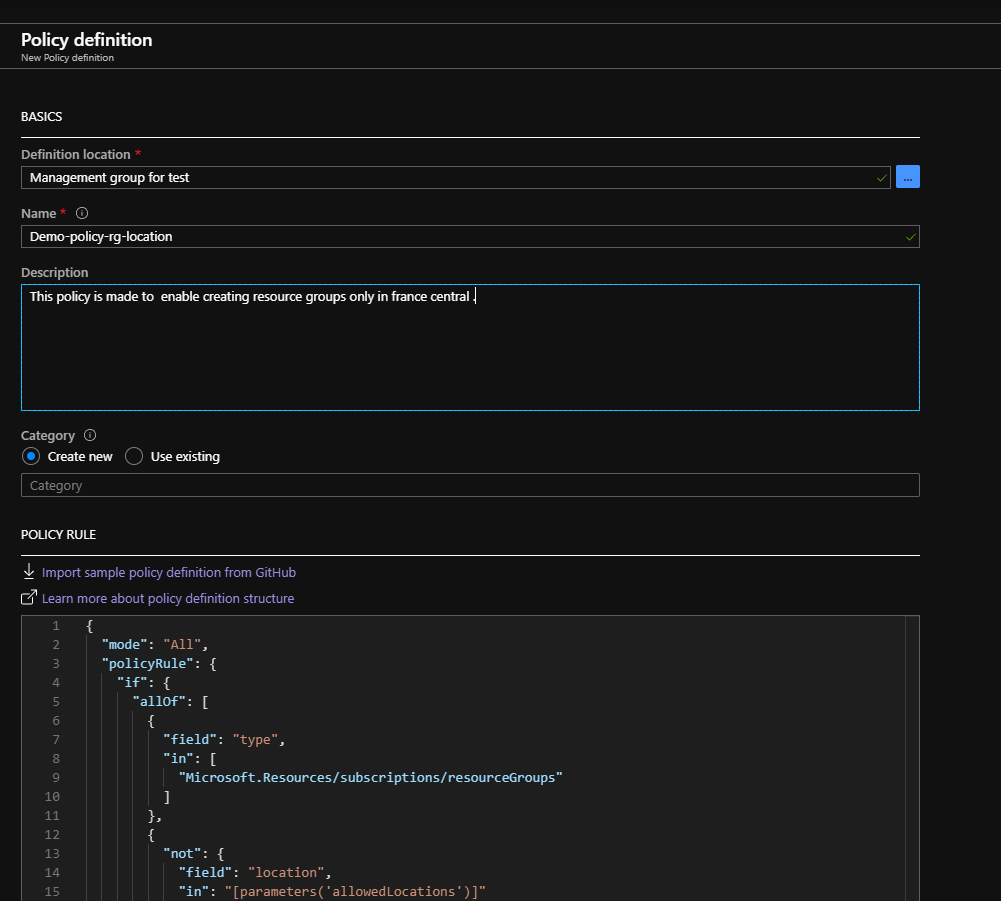
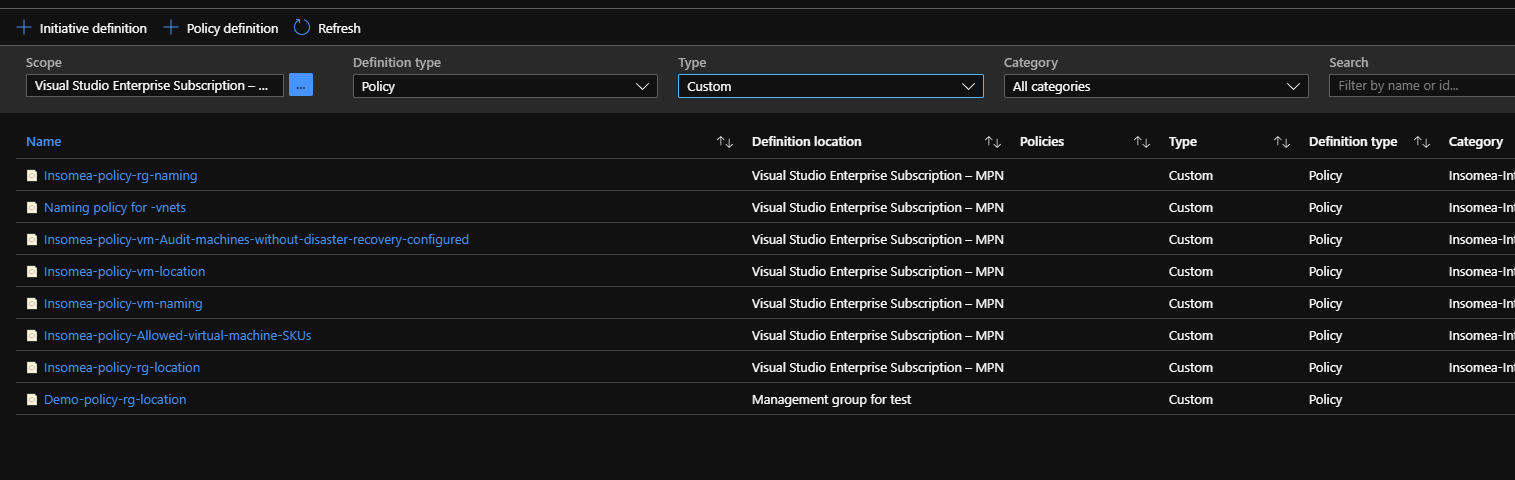
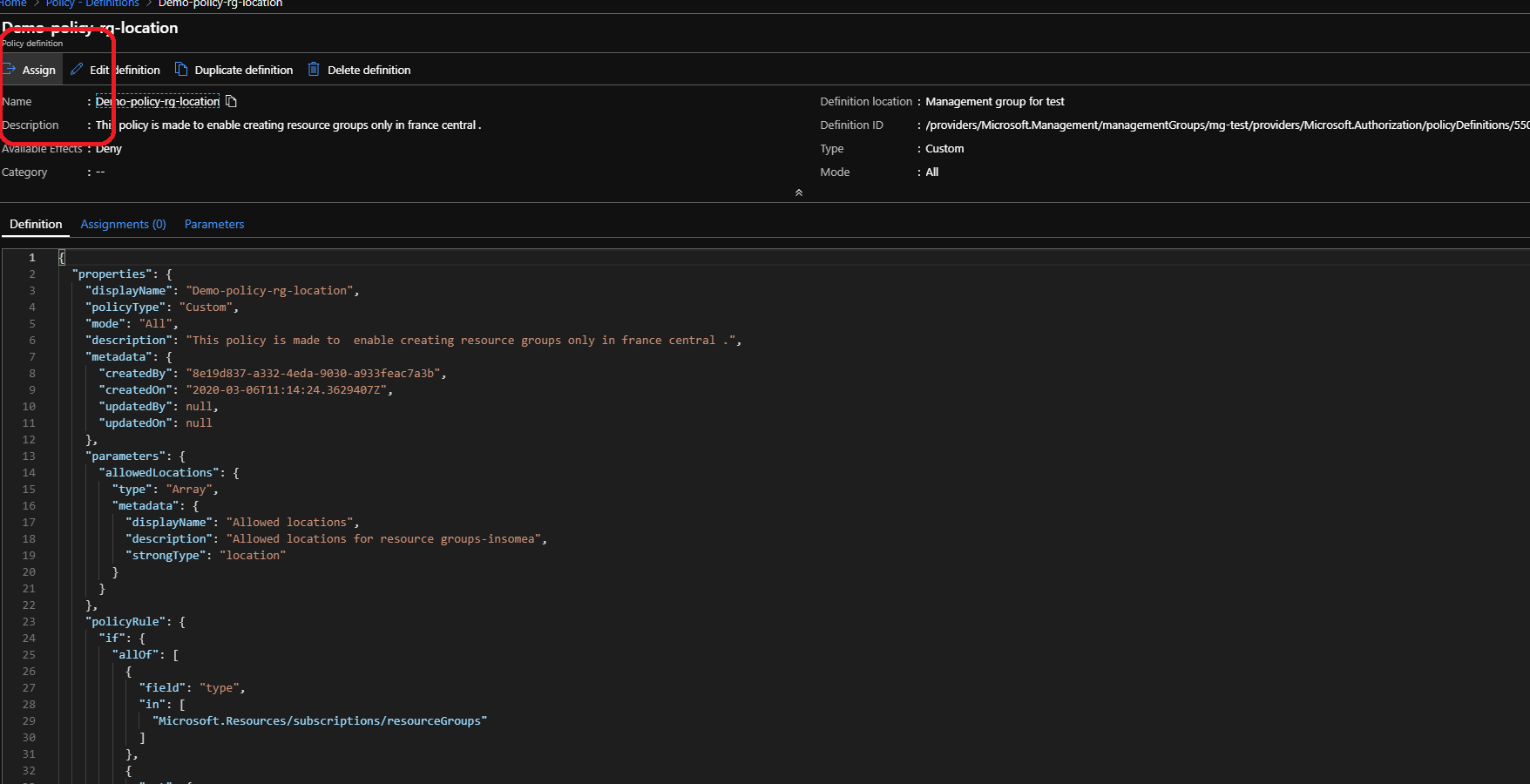
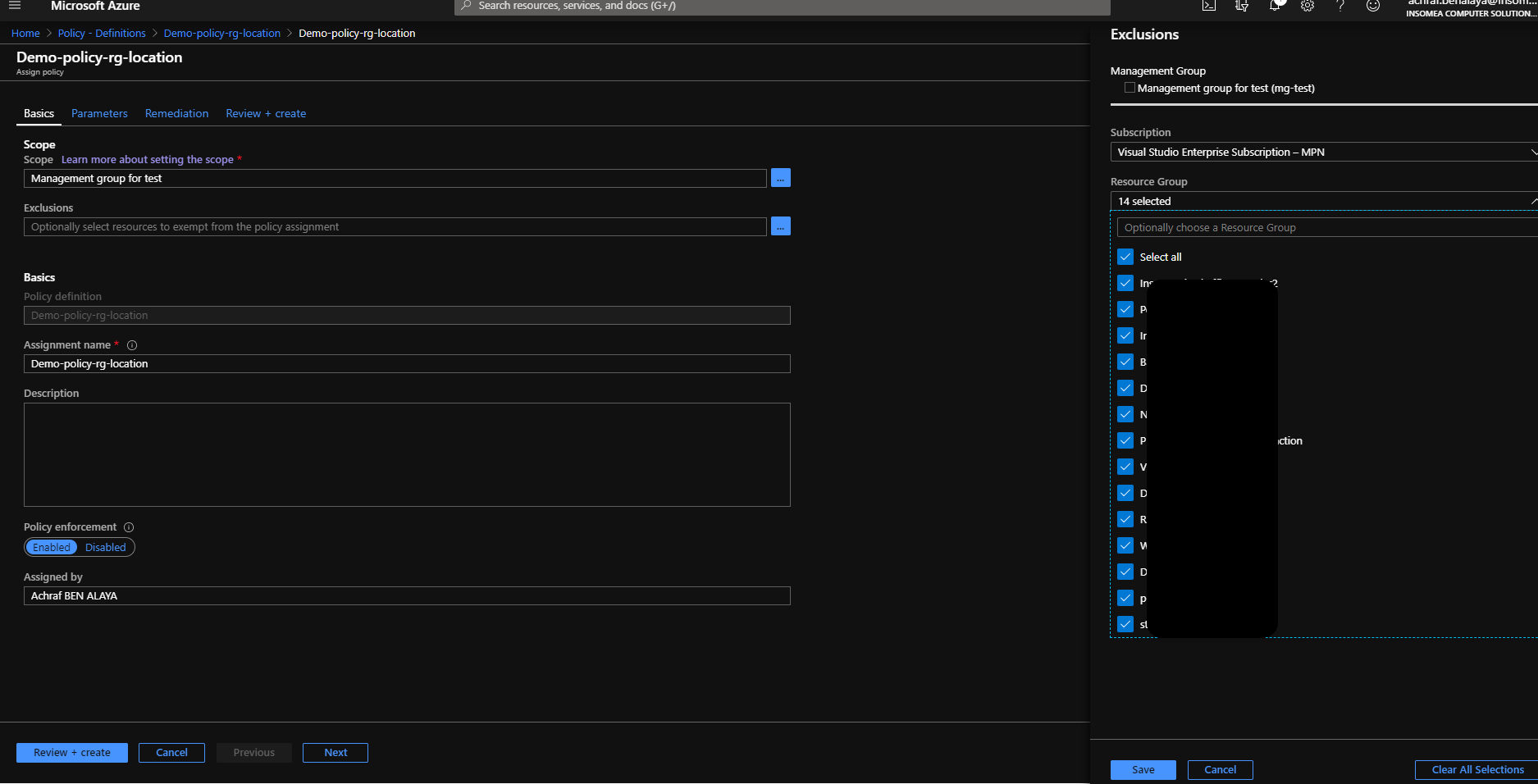
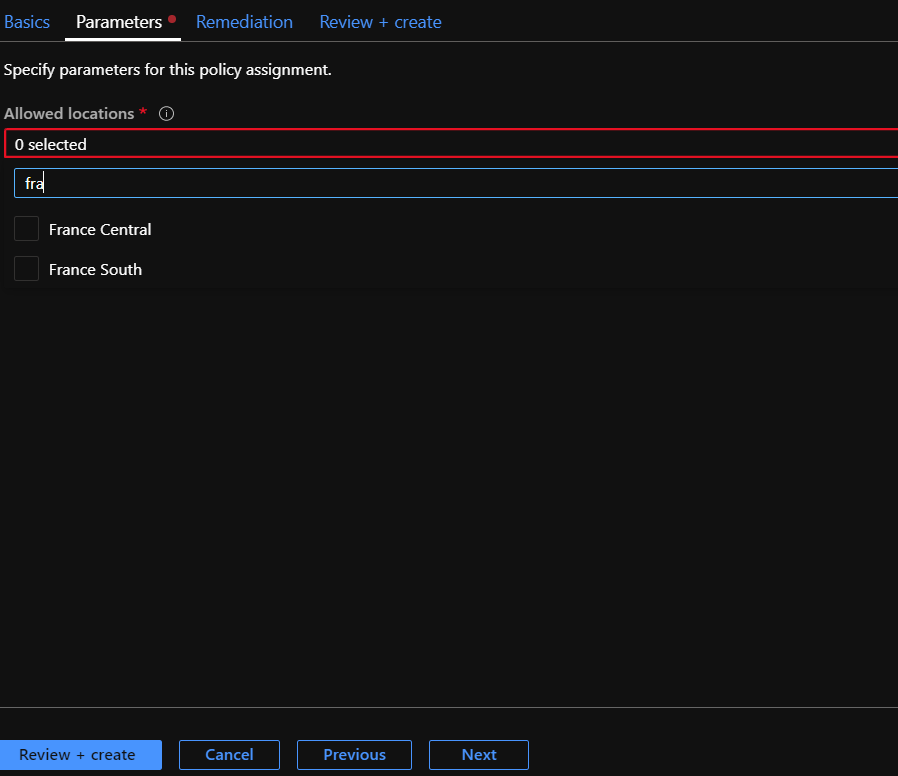
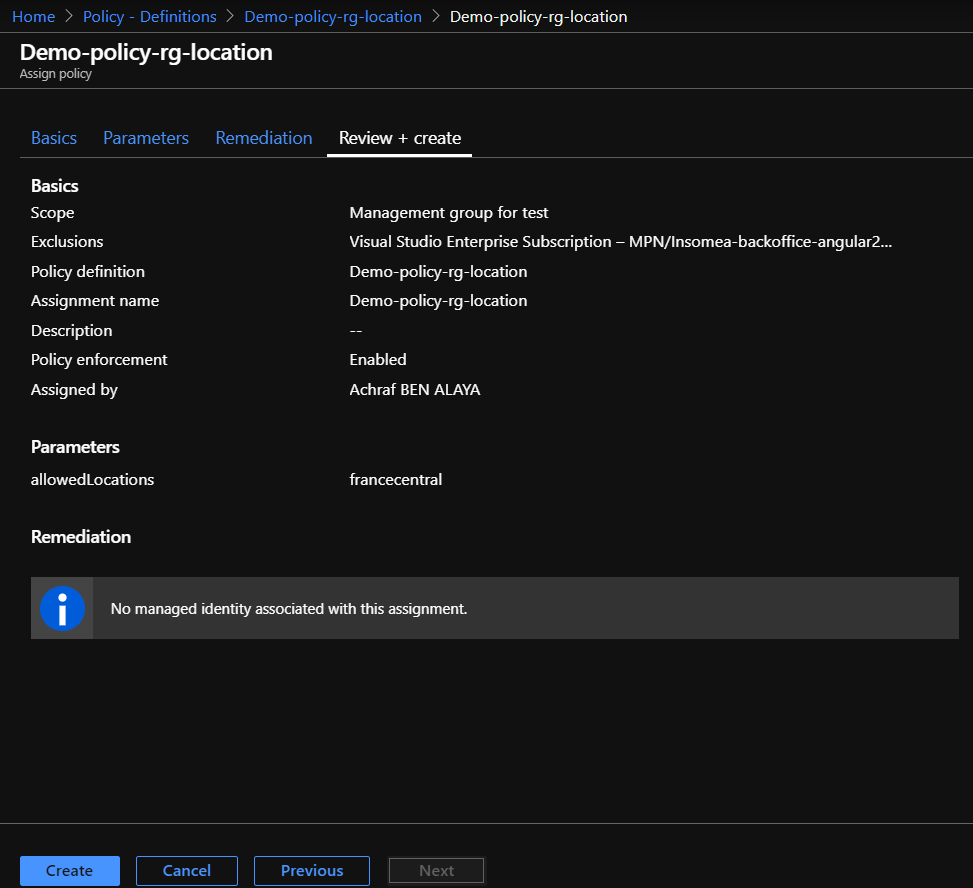
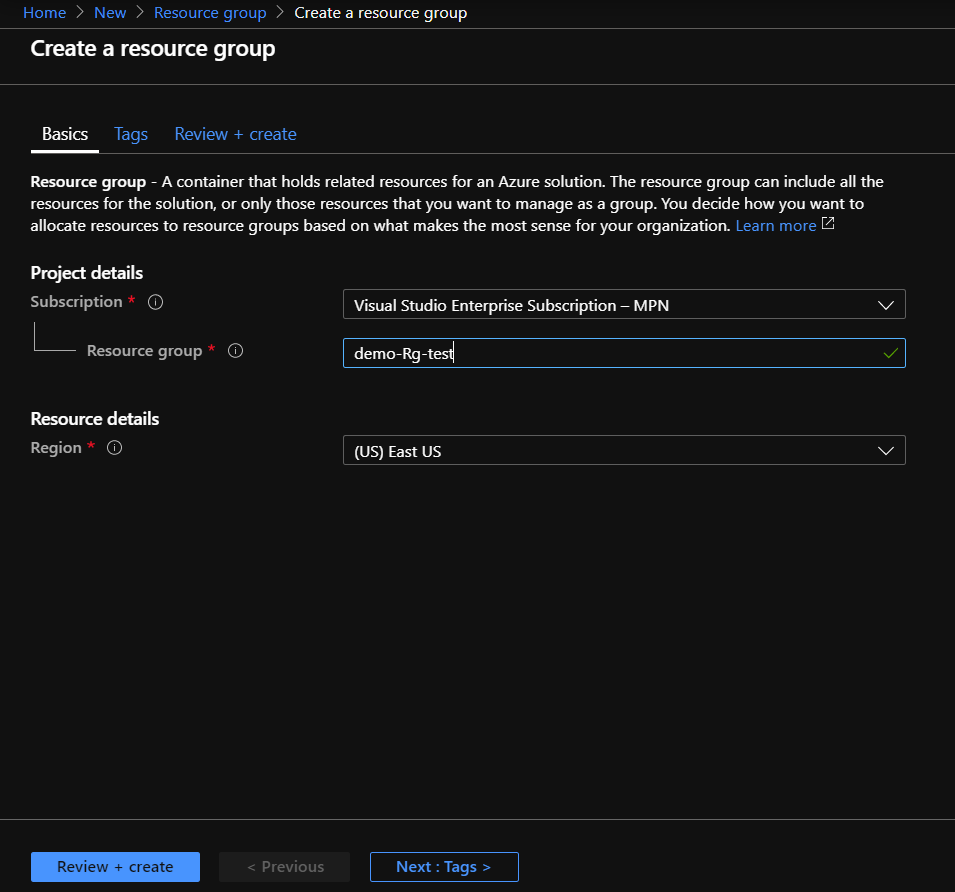
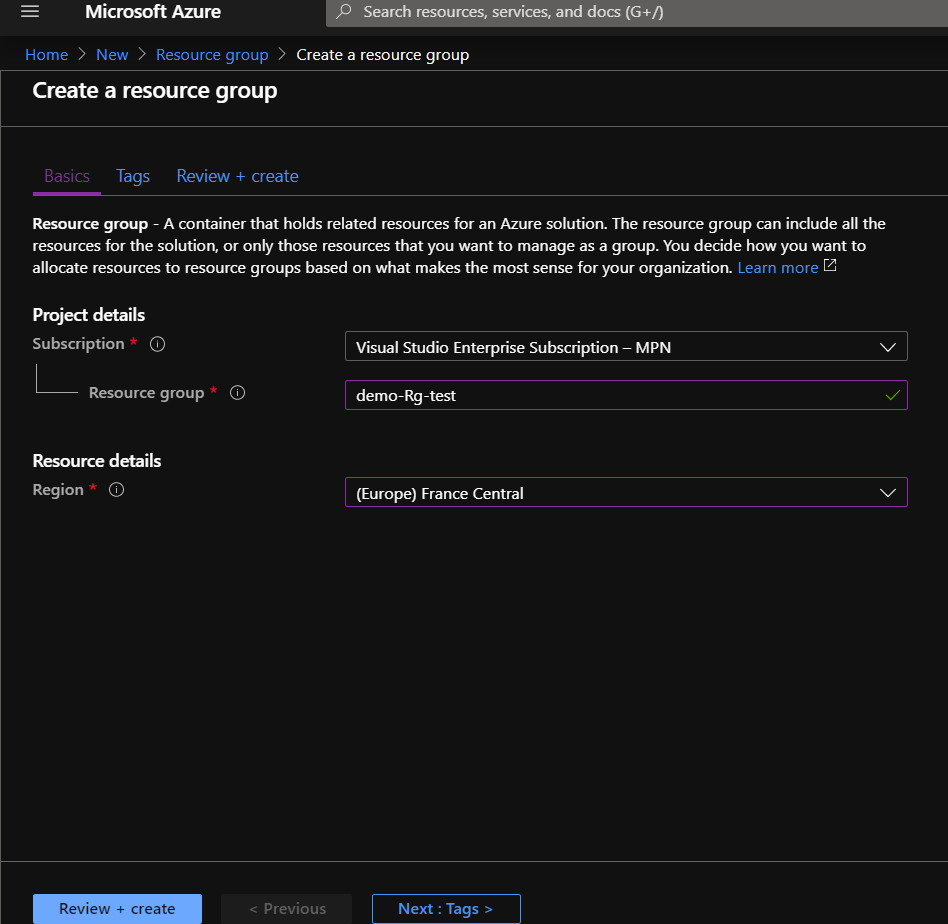
Policy 2 Allowed locations for websites:
{
"mode": "All",
"policyRule": {
"if": {
"allOf": [
{
"field": "type",
"in": [
"Microsoft.Web/sites"
]
},
{
"not": {
"field": "location",
"in": "[parameters('allowedLocations')]"
}
}
]
},
"then": {
"effect": "deny"
}
},
"parameters": {
"allowedLocations": {
"type": "Array",
"metadata": {
"displayName": "Allowed locations",
"description": "Allowed locations for Websites",
"strongType": "location"
}
}
}
}
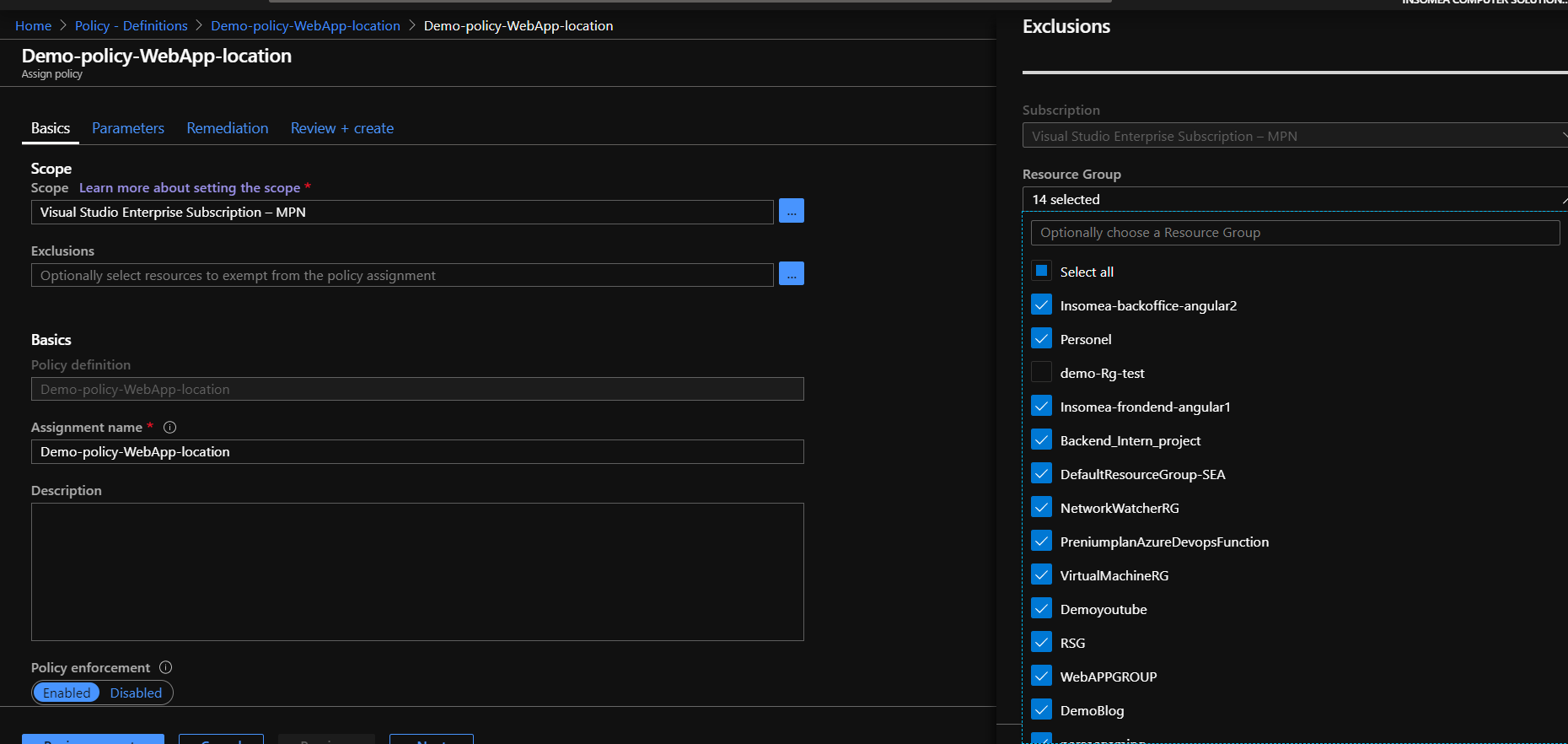
If you try to create a website in a different region , you will be denied and get this error .
NAMING POLICY
Many forget about namings their ressources and forget how important it is . But if you have the experience and have created a couple of ressources you will understand the importance of naming conventions . Giving a meaningful name to a ressource will make your life easier ,think about it ,if you have someone created a resource in your production envirmnoment and named it : blackswanWebApp and another one called it topgunwebapp ,so which one is the real app and how you will know ?
So , let’s write a naming convention for virtual machine ,let’s say you want any new virtual machine created must be named like this :
vm-p-sql-vm001 as p for prod and sql is for it’s role and vm001 is the number
so let’s define our policy now :
{
"mode": "All",
"policyRule": {
"if": {
"allOf": [
{
"field": "type",
"in": [
"Microsoft.Compute/virtualMachines",
"Microsoft.ClassicCompute/virtualMachines"
]
},
{
"not": {
"field": "name",
"match": "vm-?-???-vm###"
}
}
]
},
"then": {
"effect": "deny"
}
},
"parameters": {}
}
naming pictures
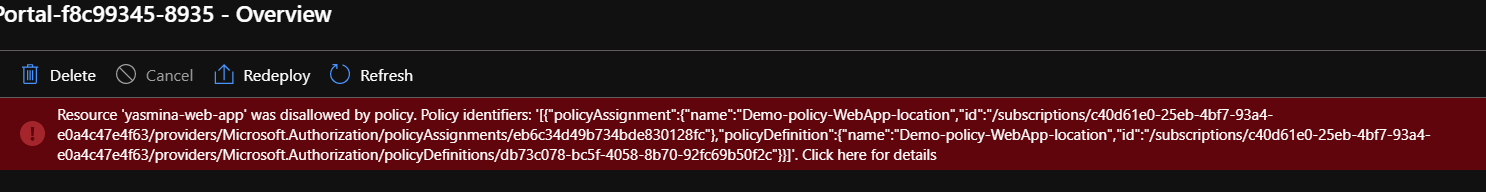
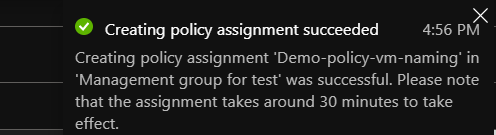
If you don’t respect the convention you will get this erro :
Else , it will be valid :
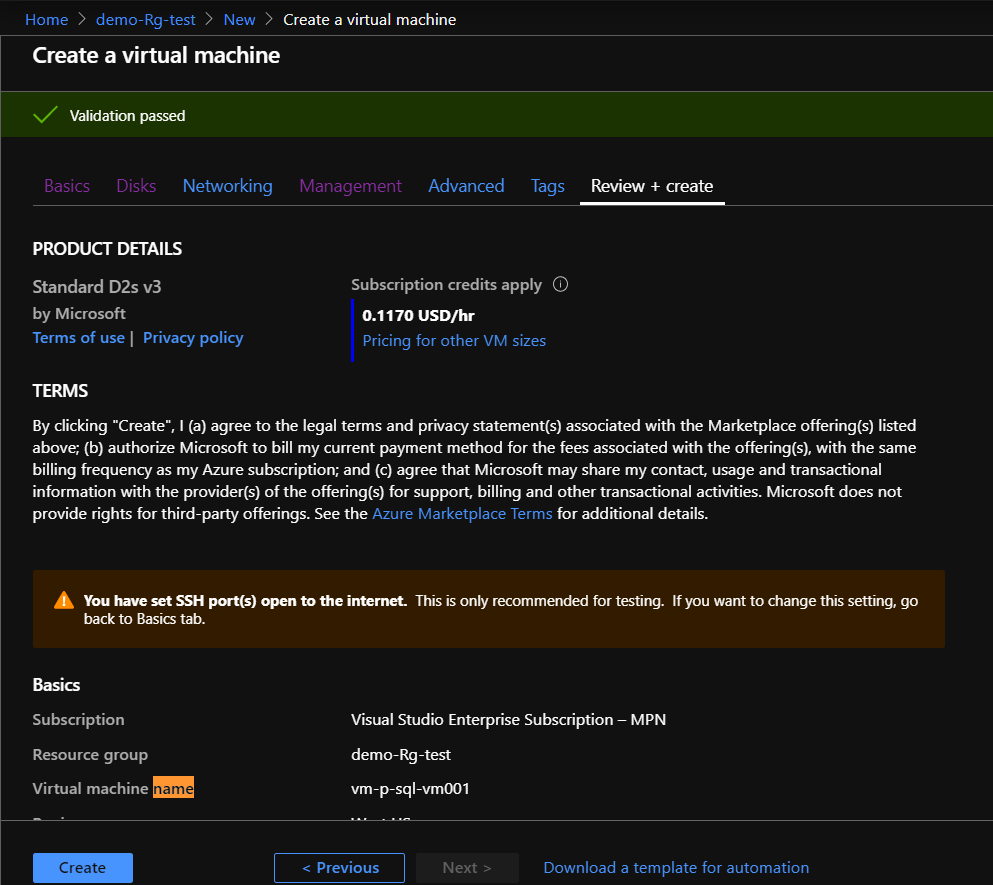
I recommend to start first by creating naming policies ,and test them cause they take time to be applied .
Later you can work on other type of policies .
Microsoft suggests using the following pattern for naming subscriptions: <Department (optional)> <Product Line (optional)>
But you could always define your patterns and keep your abbreviations as short as possible like :
vm for virtual machines ,st for storage , rg for resource groups ..
ps : keep in mind that you can’t rename resource in azure without deleting it and then recreating it with the new name .
Audit :
One of the pre-built policies is :
Latest TLS version should be used in your Web App
{
"properties": {
"displayName": "Latest TLS version should be used in your Web App",
"policyType": "BuiltIn",
"mode": "Indexed",
"description": "Upgrade to the latest TLS version",
"metadata": {
"version": "1.0.0",
"category": "App Service"
},
"parameters": {
"effect": {
"type": "String",
"metadata": {
"displayName": "Effect",
"description": "Enable or disable the execution of the policy"
},
"allowedValues": [
"AuditIfNotExists",
"Disabled"
],
"defaultValue": "AuditIfNotExists"
}
},
"policyRule": {
"if": {
"allOf": [
{
"field": "type",
"equals": "Microsoft.Web/sites"
},
{
"field": "kind",
"like": "app*"
}
]
},
"then": {
"effect": "[parameters('effect')]",
"details": {
"type": "Microsoft.Web/sites/config",
"name": "web",
"existenceCondition": {
"field": "Microsoft.Web/sites/config/minTlsVersion",
"equals": "1.2"
}
}
}
}
},
"id": "/providers/Microsoft.Authorization/policyDefinitions/f0e6e85b-9b9f-4a4b-b67b-f730d42f1b0b",
"type": "Microsoft.Authorization/policyDefinitions",
"name": "f0e6e85b-9b9f-4a4b-b67b-f730d42f1b0b"
}
Azure provides some ready made policies out of the box, all you need to do is configure these and apply them to your required scope Samples : https://github.com/Azure/azure-policy/tree/master/samples